Problem: As part of my OAuth process I need to swap and authorisation code for an Access Token using an API, the issue is that I need to get the token into PowerApps.
Initial Hypothesis: Initially I created an Azure Function that does the API post as it was the easiest. But I reverted and thought it must be easier for me to have fewer working parts and as my solution used Power Automate and I've previously used Power Automate with the HTTP custom connector I'd use the same approach. It proved fairly tricky to get the HTTP connector to work but with some playing around and clarification of my thinking it became rather straight forward.
Firstly, I need to ensure the API is working, so I use Postman:
 |
| Postman POST request using form-urlencoded. |
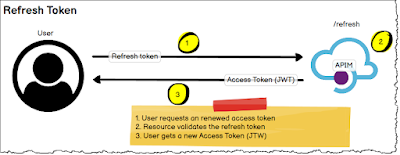
Solution: From the raw HTTP trace, I realised I needed to post the body in Power Automate in the correct format. Key value pairs for parameters and separate with an Ampersand. Also, Url's need to be escaped/encodes, in C# there are functions to encode and decode. I needed to do the encoding using Find() and Replace() methods (sic). From Power Automate, I return the Access token, refresh token and other info back to Power Apps.
More Info:
Uri.UnescapeDataString(String) Method (System) | Microsoft Docs
Understanding HTML Form Encoding: URL Encoded and Multipart Forms - DEV Community