Overview: Modern security makes automating logins requiring MFA rather difficult. This post looks at possible approaches to automate the login.
Option 1. Turn off MFA—not really, but you can set a conditional rule in EntraId to not perform MFA. This is not an option in many enterprises.
Option 2. Time-based One-Time Password (TOTP)—Microsoft Authenticator makes this pretty difficult. At least I can't do it, as the APIS are relatively limited. This is kind of expected, as it's a security measure.
Option 3. Programmatically acquire an access token without browser automation, use MSAL with a client secret or certificate (for confidential clients).
Option 4. Use Playwright to record the login and intercept the access token once logged in. Then you can store it and use it. There are a few easy options to get the session:
4.1. Retrieve the access token from the response once logged in
4.2. Retrieve from your local storage:
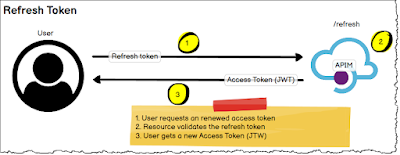
- Store the refresh token in Azure Key Vault (AKV).
- Your app retrieves the refresh token from AKV.
- Uses the refresh token to get a new access token.
- Store the new access token to run my ALM/CI/CD playwright tests
Playwright Series
Playwright Post 1 - Overview of E2E testing using Playwright
Playwright Post 2 - Continuously Test/Monitor Canvas apps and website with MFA enabled
Playwright Post 3 - Add App Insights logging inside your Playwright tests
Playwright Post 4 - 6 Min walkthru of Playwright testing with Azure Monitor
Playwright Post 5 - Understanding how Playwright works
Playwright Post 6 - Unattended testing when secured with MFA (this post)