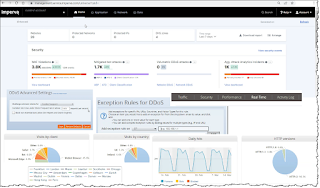
Microsoft has the "Azure DDoS Sentinel" service that can help protect your network endpoints from DDoS attacks. Common DDoS attacks all basically use hundreds of bad actors to flood traffic into you architecture to overwhelm them. Restricting traffic from the bad actor sources is key. Mixing the Azure DDoS Sentinel Service with Azure WAF, allows us to identify the bad actions and just block these bad attackers.
DDoS - Increasing, multiple bad actors try overwhelm your resources. Rate limiting can help, but ideally you want to let thru valid traffic and block bad traffic. Azure DDoS Sentinel service can be coupled with WAF to protect correctly from DDoS attacks. Normally UDP flood attacks, also protects HTTP(s) flood and TCP Flood attacks. Covers level 3-4 layer attacks.
Two SKU's:
- DDoS network protection: used on a VNet, service will work out and protect your public nodes. Can put this in from for Azure WAF are Azure Firewall, After Front Door.
- Cheaper Alternative is the DDoS IP protection, has most of the features and if only specific IP, like a web traffic IP it's a good option.