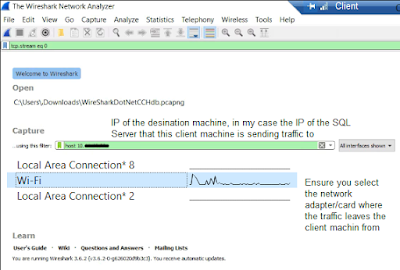
Azure Application Gateway is a http traffic load balancer that allows me to manage my web traffic. So based on urls, paths, the traffic can be pushed on accordingly. It also provides for sticky sessions. In my head I see Azure Application Gateway as a layer 7 HTTP Load Balancer and a Web Application Firewall (WAF). There are 3 core concepts: Front-ends, rules and backends that are used to route traffic from the front-end to the back-ends.
Azure Load Balancer works at level 4 where Azure application gateway is for web traffic at layer 7 of the OSI model.
Azure Front Door is basically for world wide Application gateway functionality.
Checklist on the Application Gateway:
- You should enable the WAF unless you already use another WAF like Imperva enterprise wide, do this under the "Web application firewall" option, setup OWASP rules.
- Config session affinity, and HTTPS termination using the "HTTP settings".
- "Listeners" are what listens for incoming http requests.
- "Rules" bind the listeners to the backend pools.
- "Backend pools" are used to point traffic to the end points. Also remember to setup "Health Probes", this allows the App pool to verify the backends are working.
- Ensure you set the diagnostics logging to send logs to "Log Analytics" so you can examine the logs.
Features:
- SSL/TLS termination - Terminate SSL using certificate
- Autoscaling - increase the size or instance count based on traffic requirements
- Can be setup to be zone redundant
- Static IP address that doesn't change
- WAF and DDoS (pretty new 2022, applied using Azure DDoS Sentinel service) capabilities - The WAF allows you to apply OWASP rules and add additional custom rules. Bot protection is also built in, rules need to be applied to get it to work.
- URL-based routing
- Multiple domains/site hosting
- Redirection
- Sticky sessions/session affinity
- HTTP/2 support
- Custom error pages (so useful)
- Rewrite headers and URL
References: